Which Best Practices Can Help Defend Against Social Engineering Attacks
Report the incident immediately. By implementing strict user authentication and IP authorization at the gateway you can take this opportunity away from the attacker.

Best Practices For Lowering Cyber Insurance Costs And Cyber Risk
Enable a policy that states that the IT department should supply information over the phone only to managers.

. Choose three What type of network security test uses simulated attacks to determine the feasibility of an attack as well as the possible consequences if the attack occurs. Acting overly friendly or eager. Like automated network-defense systems that identify and repel new viruses without human interaction a security-aware culture helps employees easily and routinely identify and.
One way to reduce the threat of social engineering attacks is to put security awareness at the top of your agenda. Up to 20 cash back When we think about cyber-security most of us think about defending ourselves against hackers who use technological weaknesses to attack data networks. Educate employees regarding policies Resist the urge to click on enticing web links.
Social Engineering Attacks. If you can get. Social engineering is an attack vector that relies heavily on human interaction and often involves manipulating people into breaking normal security procedures and best practices in order to gain access to systems networks or physical locations or for financial gain.
Be suspicious of people you dont know who ask for sensitive information. This is fairly common sense but ensure that you have policies in place to never disclose passwords. Do whatever it takes to ensure your employees are fully aware of these policies so they adhere to them carefully.
Some security software is available to combat phishing and pharming but the best defense against the full range of social-engineering attacks is a corporatewide culture of security awareness. Enable a policy that states that the IT department should supply information over the phone only to managers. Immediately change all of your passwords.
More often than not a healthy cybersecurity posture is based on human behavior. What are the two most effective ways to defend against malware. Always be mindful of risks.
Install and maintain anti-virus software firewalls and email filters. Hold regular conferences set up workshops and develop guidelines on how to protect against social engineering attacks. Deploy well-designed firewall appliances.
But theres another way into organizations and networks and thats taking advantage of human weakness. 10 Ways to Prevent Social Engineering Attacks 1. Social engineering is all about manipulating behavior.
All social engineering attacks involve pretexting but this is especially true for in-person attacks. Do not provide password resets in a chat window. Refer to the exhibit.
2 2 pts What three best practices can help defend against social engineering attacks. Planned and methodical policies are a simple yet incredibly effective defense against social engineering attacks. What three tasks can a network administrator accomplish with the Nmap and Zenmap security testing tools.
Confidential data intellectual property and digital systems are only as secure. Choose three Add more security guards. Choose three Deploy well-designed firewall appliances.
Here are six tips to help your organization prevent social engineering attacks. Choose three-Enable a policy that states that the IT department should supply information over the phone only to managers-Educate employees regarding policies-Add more security guards-Do not provide password resets in a chat window. Question 15 What three best practices can help defend against social engineering attacks.
Social engineering attacks involve the psychological manipulation of users to gain their trust and coax them into taking actions that they otherwise wouldnt. A few of the warning signs include. To avoid falling prey to social engineers always maintain a healthy sense of skepticism about anyone asking for sensitive information.
For instance revealing sensitive information giving away passwords downloading malware purchasing contraband and so on. If you think you are a victim of a social engineering attack. This how-to will suggest some best practices to help you reduce the risk of a social engineering attack against your organization being successful.
Making sure your entire workforce understands the various tricks of cybercriminals can be your best defense against social engineering. Double check triple check any request you get for the correct information. What three best practices can help defend against social engineering attacks.
One of the best ways to protect against social engineering is to understand the warning signs and steer clear of attacks. Resist the urge to click on enticing web links. Asking to verify your information.
Clothes make the man and social engineers know that dressing talking and acting the right way can do wonders for getting sensitive information out of unsuspecting targets. Add more security guards. Install maintain and update regularly your anti-virus software firewalls and email filters.
Asking for immediate assistance. What three best practices can help defend against social engineering attacks. Contact your financial institution and monitor your account activity.
This is known as social engineering which involves tricking someone into divulging. Look out for cybersecurity news to take swift actions if you are affected by a recent breach. Set your automatic updates on if you can and only access secured websites.

Login Security 7 Best Practice For Online Security Loginradius Blog

Top 22 Security Information And Event Management Software In 2022 Reviews Features Pricing Comparison Pat Research B2b Reviews Buying Guides Best Practices
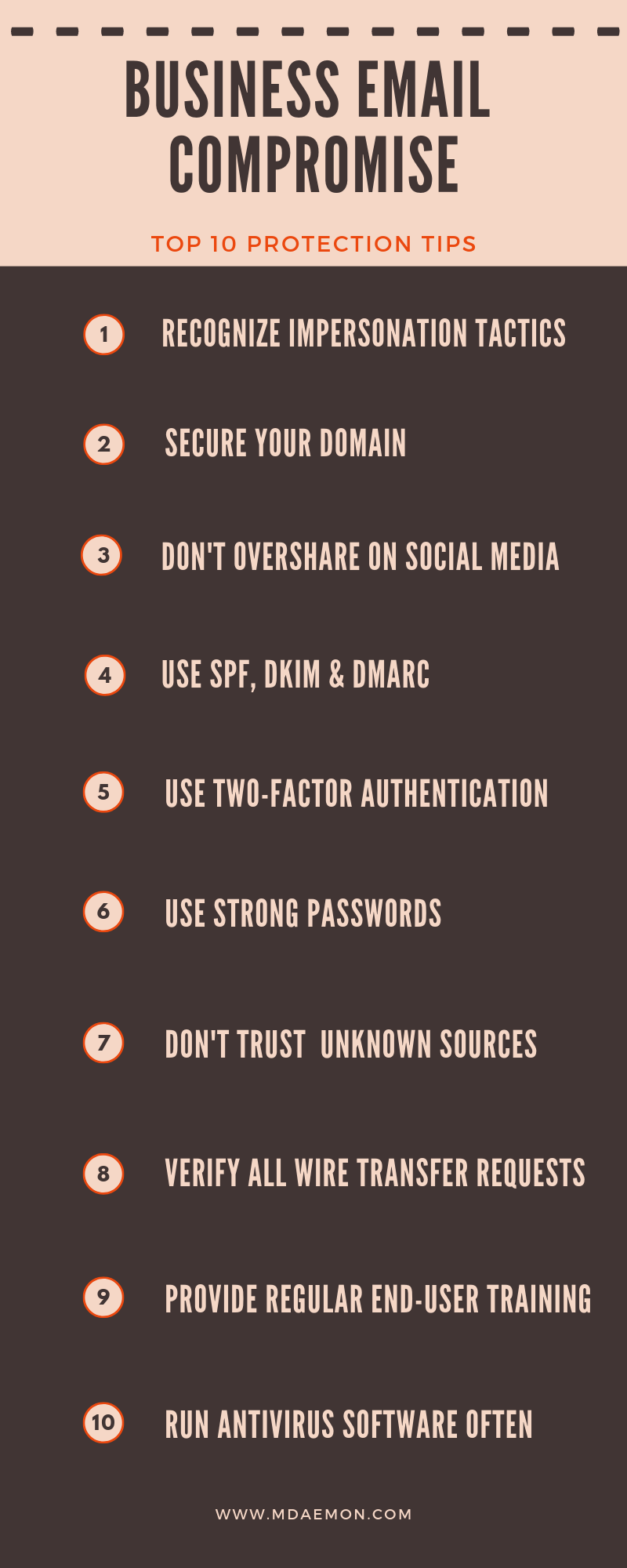
Best Practices To Avoid Business Email Compromise Ceo Fraud Attacks

5 Best Practices For Your Incident Response Plan Exabeam

11 Best Practices For Developing Secure Web Applications Lrs Web Solutions

10 Ways To Reduce Cybersecurity Risk For Your Organization Upguard

Best Practices Using Web Risk Api To Help Stop Phishing And More Data Integration

What Are Some Best Practices For Ethereum Smart Contracts

Social Engineering Attacks Prevention And Best Practices Loginradius Loginradius Blog
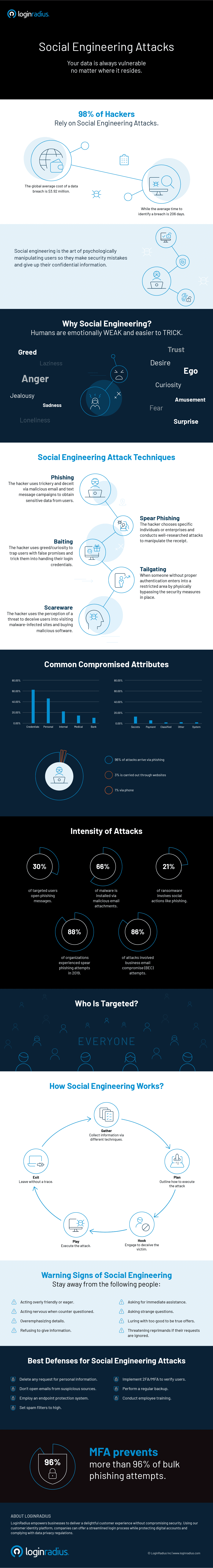
Social Engineering Attacks Prevention And Best Practices Loginradius Loginradius Blog

7 Best Practices For Securing System Administrator Privileged Account Ekran System

Introduction To Software Security And Best Practices

7 Best Practices For Securing System Administrator Privileged Account Ekran System

Best Practices For Enterprises To Prevent Social Engineering Attacks Eweek

Security Best Practices For Staff

What Is Email Security Definition Benefits Examples Best Practices Toolbox It Security

13 Cyber Security Best Practices To Prevent And Respond To Cyber Attacks
![]()
Social Engineering Attacks Prevention And Best Practices Loginradius Loginradius Blog
